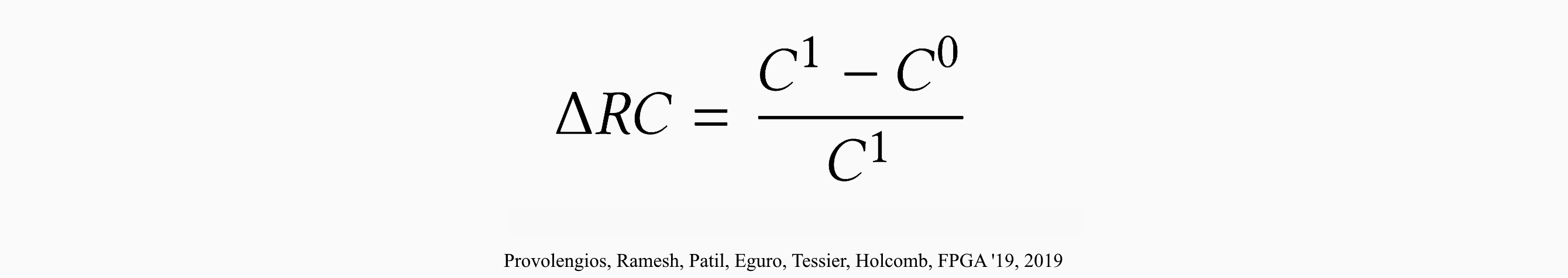Week 1 Rundown
Hittin’ the Books
This week I looked at 3 papers regarding virtual FPGAs and possible vulnerabilities. Those papers are:
- “RAM-Jam: Remote Temperature and Voltage Fault Attack on FPGAs using Memory Collisions”, Alam et al.
- “Characterization of Long Wire Data Leakage in Deep Submicron FPGAs”, Provolengios et al.
- “Oscillator without a combinatorial loop and its threat to FPGA in data centre”, Sugawara et al.
Each provided helpful insight to begin my research and interesting findings that I will need to consider going forward. Here we’ll explore each of the papers in detail.
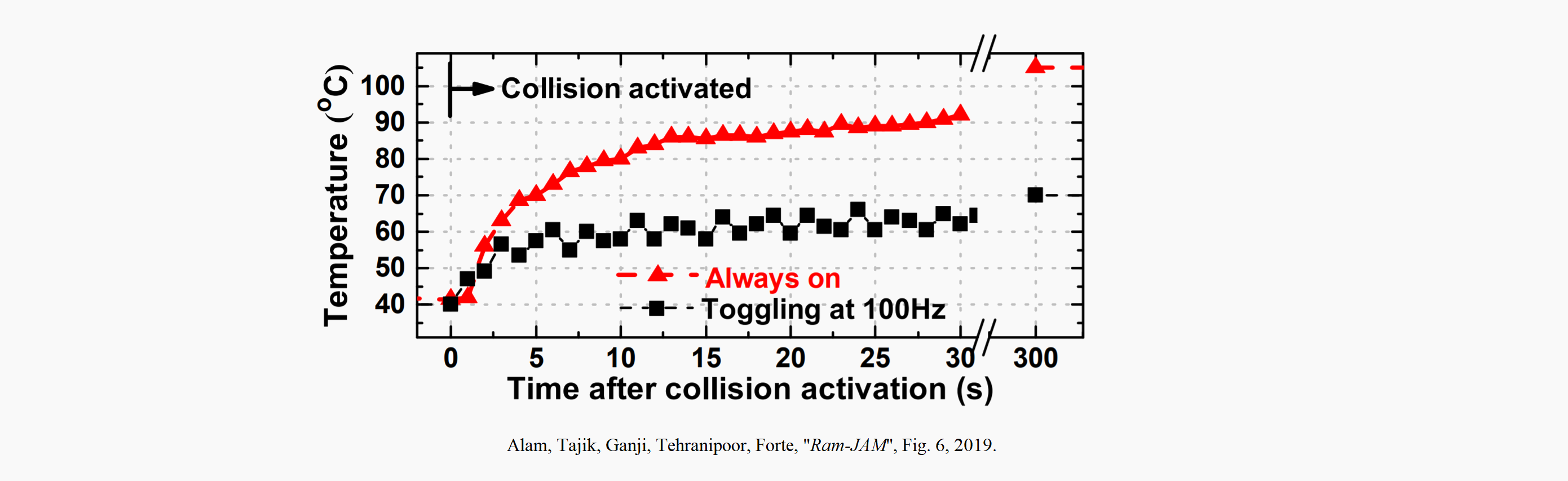
[1] Alam et al.
In this study, researchers discuss their work in a SRAM memory fault injection attack. By wiring up look-up-tables to function as dual port RAM locations [1]. are able to toggle memory write collisions, causing a slight rise in chip temperature when done. They initially focused on toggling the collisions very quickly and the chip temperature rose beyond the point of functioning correctly. However, they successfully determined the existence of collision frequencies that raise the chip temperature without being easily detected. This is where the danger of the attack comes from; It has the ability to cause hardware damage and bit-flips, but also carry out the attack stealthily.
[2] Provolengios et al.
What’s most interesting to me about this paper is the use of ring oscillators. I got my first look into how studying frequency of the oscillator can provide much more data than we realize given the right scenario. For instance, the study was conducted on a multi-tenant FPGA, which has become more and more common in the cloud. If one user wires a RO into their FPGA and the placement is such that one wire is adjacent to a long wire of another user’s section, the RO frequency will be measurably effected by the other user. The researchers conducted this experiment by sending straight logic 0s across the alternative user’s long wire and again with logic 1s, all while measuring the count of a bit counter being drive by the RO.
By measuring small changes in delay “on the order of femtoseconds”, researchers found that they could detect significant data leakage in long wires from the RO frequency change. They determined that “leakage can be avoided by disallowing multiple tenants to share use of a single channel” [2].
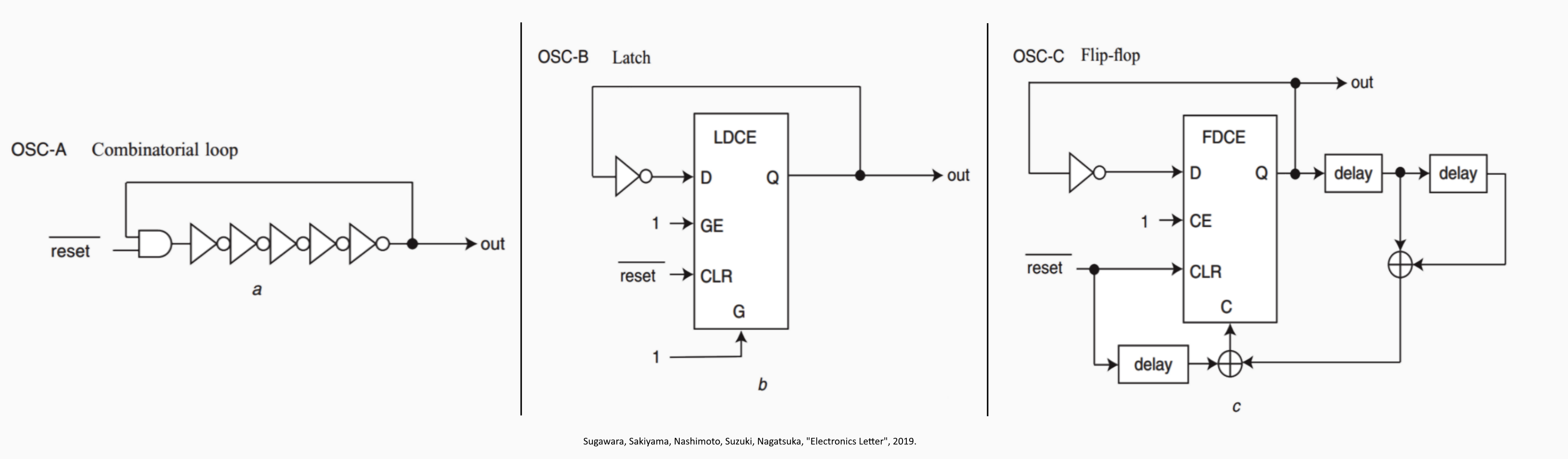
[3] Sugawara et al.
I enjoyed reading this letter a lot! The idea behind it is this: there are a plenty of attacks on virtual FPGAs that use combinatorial loops (feedback loops) that behave successfully, but in a lot of actual virtual FPGA data centers they don’t allow a user to create a combinatorial loop at all. The letter then goes into how they were able to create “oscillators without a combinatorial loop” that till allow for all the same attacks [3]. It was greatly interesting to see how the complexity of the oscillator used (shown above) grows but is necessary to remain allowed within current FPGA rules and guidelines.
Next week, I’ll start working with Verilog and see how far I get with it. I’ll be using the ISE Design Suite to develop my projects.
Works Cited
[1] M. M. Alam, S. Tajik, F. Ganji, M. Tehranipoor, and D. Forte, “RAM-Jam: Remote Temperature and Voltage Fault Attack on FPGAs using Memory Collisions,” in 2019 Workshop on Fault Diagnosis and Tolerance in Cryptography (FDTC), Aug. 2019, pp. 48–55, doi: 10.1109/FDTC.2019.00015.
[2] G. Provelengios, C. Ramesh, S. B. Patil, K. Eguro, R. Tessier, and D. Holcomb, “Characterization of Long Wire Data Leakage in Deep Submicron FPGAs,” in Proceedings of the 2019 ACM/SIGDA International Symposium on Field-Programmable Gate Arrays, Seaside, CA, USA, Feb. 2019, pp. 292–297, doi: 10.1145/3289602.3293923.
[3] T. Sugawara, K. Sakiyama, S. Nashimoto, D. Suzuki, and T. Nagatsuka, “Oscillator without a combinatorial loop and its threat to FPGA in data centre,” Electronics Letters, vol. 55, no. 11, pp. 640–642, Apr. 2019, doi: 10.1049/el.2019.0163.